Security
To ensure the security of Agiloft and the server it is run on, you should take the following steps:
Use complex passwords
Passwords that are resistant to attack should be at least 8 characters in length, contain a mixture of upper and lower-case characters, contain one or more numbers or other non-alphabetic characters, and not be derived in any obvious way from the username. All staff accounts should be secured with such passwords, especially those in the Admin group. If it is desired to give end-user accounts simple passwords for user convenience, then these accounts should be severely restricted in what they may do (for example only filling out a single form). End-user accounts with the ability to modify existing records or view sensitive data should also be given attack-resistant passwords.
Change the password
Change the password of the Admin Console and default KnowledgeBase users. These default passwords are well-known, and are an extremely easy method of attack.
To change the Admin Console password, do the following:
- Log in to the Admin Console:
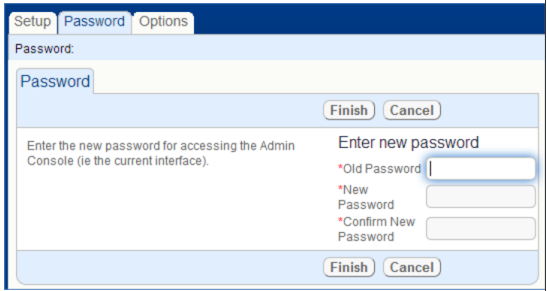
- Select the Password tab:
- Enter the existing and new passwords and click Finish.
Sample Users
Each knowledgebase you create is automatically populated with a number of sample users:
The users: Anonymous, faquser , register are essential to certain functionalities. Users like admin and ewsystem should have their passwords changed to be more secure. Remaining users should be deleted, as they are probably not relevant to your organization.
The ewsystem user is used by Agiloft customer support staff to assist customers.
To change the password:
- Log into a knowledgebase and select Contacts > View Contacts, as shown above.
- Click the Edit icon to edit the user's information, and select the Account Info tab:
- Enter the new password in the fields and click Finish.
Assign users to Agiloft groups carefully.
Users should not be assigned privileges they do not need or do not have the skills to use safely. For example, a user with the ability to delete all records in a table in one operation can do considerable damage accidentally if they are not familiar enough with Agiloft. Users in the admin group should only be those trusted and skilled enough to make structural changes in a knowledgebase.
Use SSL
Use SSL (via HTTPS) to secure Web browser connections to the Agiloft server. Using standard HTTP to connect to the Agiloft server exposes passwords and potentially sensitive information to anyone able to monitor network traffic, and opens up additional methods of attack to those able to intercept network traffic.
To connect to your Web server using SSL, you will need to configure it, as it is not the default configuration. You will need to purchase or generate a server certificate that authenticates your server to the clients. This configuration differs depending on the host operating system type and release, and the Web server software in use. The following resources may help:
Securing Your Apache 2 Server with SSL
Van's Apache SSL/TLS mini-HOWTO
Even if you must allow access to some accounts through standard HTTP, ensure that HTTPS is used to access more sensitive accounts such as those in the admin group of knowledgebases and the Admin Console.
Restrict login access to the Agiloft server machine.
A root user on Unix/Linux or a user in the Administrators group on Windows can circumvent
Agiloft internal security by modifying program and data files or directly changing data in the database, including passwords. But even a regular unprivileged user can circumvent security by using local Web access to use special debugging features of
Agiloft (such as the JMX console, as shown below) that are not accessible to connections from outside the server.
Restrict services accessible on the Agiloft server.
Treat the Agiloft server as you would any other sensitive server by only allowing connections essential for Agiloft operation, such as HTTP and HTTPS, and administration, such as ssh (Unix/Linux) or Terminal Services (Windows). Other services or applications run on the same server machine, including other Web applications, could potentially contain security holes which could lead to the compromise of Agiloft data.
The default services installed with most recent Linux distributions are generally minimal. You should use the nmap tool to verify which ports are exposed on your server. For example:
linux# nmap -sS wizard.example.com Starting Nmap 4.00 ( http://www.insecure.org/nmap/ ) at 2006-12-14 18:12 PST Interesting ports on wizard.example.com (10.0.0.1): (The 1667 ports scanned but not shown below are in state: filtered) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 113/tcp closed auth 443/tcp open https 8080/tcp open http-proxy MAC Address: 00:E0:81:00:00:12 (Tyan Computer) Nmap finished: 1 IP address (1 host up) scanned in 64.320 seconds linux#
These are the TCP ports normally used by
Agiloft:
80
The standard HTTP port that connects to the Apache or IIS Web server. The /gui2/ URL is forwarded to the Tomcat server and is the normal unsecured access to the
Agiloft application.
8080
The native connection port to the Tomcat server that is part of the Java framework behind
Agiloft.
443
The standard HTTPS port for Web service over SSL. This is either forwarded to the Tomcat server by the native Web server or forwarded directly to port 8443 by Linux kernel using the internal firewall module.
8443
The native HTTPS port that Tomcat may be configured to listen to. It is often better to use the SSL engine in Tomcat (with requests forwarded from port 443) than to configure the native Web server for SSL and request forwarding.
3306
The standard server port for MySQL, the default Linux back-end database, This port is not exposed externally (i.e., it is bound only to localhost).
Related articles
There is no content with the specified labels