Use this article to guide you in setting up CyberArk Workforce Identity (formerly Idaptive or Centrify Identity Service) with SAML single sign-on to manage access to a  knowledgebase. For more information on SAML configurations, see SAML 2.0 SSO. Note that the steps in this topic might vary depending on the environment in which they are being implemented. Contact
knowledgebase. For more information on SAML configurations, see SAML 2.0 SSO. Note that the steps in this topic might vary depending on the environment in which they are being implemented. Contact  support if you need more assistance.
support if you need more assistance.
To complete these steps, you need an Idaptive account with administrator access, and administrator-level login credentials for  . You can sign up for a free trial account to use for testing. . You can sign up for a free trial account to use for testing. |
Add SAML 2.0 to the Knowledgebase
The full setup requires you to switch between  and Idaptive, so open each one in its own browser window so you can easily switch between them. and Idaptive, so open each one in its own browser window so you can easily switch between them. |
First, if you don't want users to be created automatically in  when they first log in with Idaptive SAML, create the users first and assign them to the appropriate Groups and Teams.
when they first log in with Idaptive SAML, create the users first and assign them to the appropriate Groups and Teams.
When you are ready to connect Idaptive:
- Click the Setup gear in the top-right corner and go to Access > Configure SAML 2.0 Single Sign-On.
- On the General tab of the SAML Configuration wizard:
- Select Enable SAML SSO.
- Select Create SAML IdP Authenticated user in Agiloft.
- Select the last checkbox only if you want to synchronize the user attributes in Agiloft with those in the IdP every time a user logs in. If you leave this deselected, the user's attributes are synchronized only when the user is first created.

- On the Service Provider Details tab:
- Leave the first two fields as they are. They are used to fill in Idaptive fields below.
- For the next fields, Keystore file path, Java KeyStore Password, and Alias to add the certificate to the Java KeyStore:
- If you are using
 's hosted service, the fields are populated by Support.
's hosted service, the fields are populated by Support. - If you are using an in-house server where
 is installed, follow the steps in SAML 2.0 SSO under Generate a Keystore File and Configure the Identity Provider.
is installed, follow the steps in SAML 2.0 SSO under Generate a Keystore File and Configure the Identity Provider.
 Click Finish.
Click Finish. - Click Download SAML 2.0 Service Provider Metadata and save to to an accessible location.
 Click Download X.509 Certificate and save it to an accessible location.
Click Download X.509 Certificate and save it to an accessible location.
Create a Web App in Idaptive
Next, open Idaptive.
- Log in to the CyberArk Identity Admin Portal using your administrator credentials; for example, https://example0111.my.idaptive.app.
- Click Web Apps in the left pane, then click Add Web Apps.
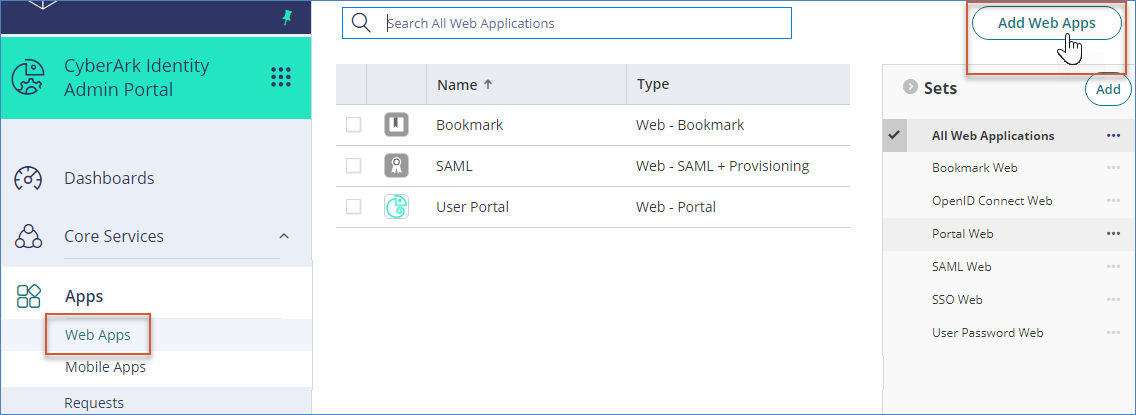
- Go to the Custom tab, scroll down, and click Add SAML. Confirm your selection.
- Close the dialog. You are automatically directed to the Application Settings window for the SAML application.
- Click Settings.
- Add a Name, Description, Category and Logo.
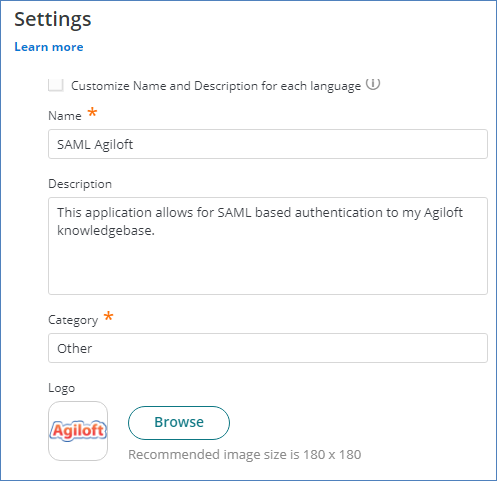
- Scroll down to the Advanced section and select the "Show in user app list" checkbox. This enables you to log in directly from the Idaptive App list.

- Click Save.
 Establish the SAML Connection to
Establish the SAML Connection to 
With these configurations in place, you can establish the connection.
- In Idaptive, click Trust.
- Now, if possible, bring up the
 window next to the Trust configuration in Idaptive, so you can go between them to fill in the values. In
window next to the Trust configuration in Idaptive, so you can go between them to fill in the values. In  , return to the Service Provider Details tab, if it isn't already open.
, return to the Service Provider Details tab, if it isn't already open. - Complete the Idaptive fields as follows:
- At the bottom, under Service Provider Configuration, click Choose File. Navigate to the metadata XML file you downloaded, select it, and click OK.
- In the Service Provider Configuration section, select Manual Configuration.
- In the Issuer field, paste the value from the Agiloft (SP) Entity ID field in
 .
. - In the Assertion Consumer Service URL field, paste the value from the SAML V2 Assertion Consumer Service (ACS) Endpoint field in
 .
. - For Sign Response or Assertion?, select Both.
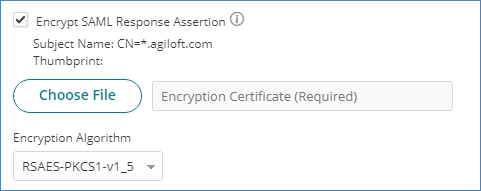
- Select Encrypt Assertion.
- If Subject Name and Thumbprint don't have a value, click Browse and navigate to the X.509 certificate you downloaded earlier. When the file is uploaded, encryption assertion details appear.
- In
 , go to the Identity Provider Details tab. In Idaptive, go to the Identify Provider Configuration section.
, go to the Identity Provider Details tab. In Idaptive, go to the Identify Provider Configuration section.- Select Manual Configuration and expand the IdP Entity ID and Signing Certificate drop-downs.
- For IdP Entity ID/Issuer, copy the URL from Idaptive into the equivalent field in
 .
. - For IdP Provided X.509 certificate contents, click Download under Signing Certificate and save the file to an accessible location. Open the .cer file in a text editor, copy the contents, and paste them into
 .
. - For IdP Login URL, copy the Single Sign On URL field from Idaptive into
 .
. - For IdP Logout URL, opy the Single Logout URL field from Idaptive into
 .
.
- In
 , click Finish. In Idaptive, click Save.
, click Finish. In Idaptive, click Save.
At this point, the initial SAML configuration is complete. Next, create Idaptive and  users.
users.
Assign Idaptive Users to the Application
If you do not already have a list of users and roles in your organization's Idaptive account, begin by defining the roles you need. Then, in Idaptive, add, invite or import them, and then set up their roles. For more information on these processes, see the CyberArk Documentation.
- Once the roles and users have been created, open Idaptive, select Web Apps, and open the SAML application.
- Click Permissions and then click Add.

- Select the roles and users you want to allow to access the
 application via Idaptive.
application via Idaptive. - Click Save.
At this point, the users who were assigned roles are now be able to access the  knowledgebase using this URL syntax:
knowledgebase using this URL syntax: https://[agiloftserver]/gui2/samlssologin.jsp?project=KB_NAME
https://server.agiloft.com/gui2/samlssologin.jsp?project=Idaptive |
In addition, a user can login to the  GUI from the Idaptive apps dashboard in the User Portal by clicking on the
GUI from the Idaptive apps dashboard in the User Portal by clicking on the  SAML application icon.
SAML application icon.
For more information on creating the Group and Team mappings in  , see Configure Agiloft. , see Configure Agiloft. |
Dynamic Group and Team Mapping
A standard configuration assigns a fixed Group and Team mapping to any new users created via  SAML SSO. However, it is also possible to allocate users to different Groups or Teams from within Idaptive.
SAML SSO. However, it is also possible to allocate users to different Groups or Teams from within Idaptive.
To set up dynamic Group and Team mapping:
- Create all of the Groups and Teams in
 . If a new Group or Team is added to the Active Directory or repository used by Idaptive, then they should also be added to
. If a new Group or Team is added to the Active Directory or repository used by Idaptive, then they should also be added to  .
. - In the CyberArk Identity Admin Portal:
- Open the Web App you created for accessing
 .
. - Click SAML Response to open the Attributes and Custom Logic screen.
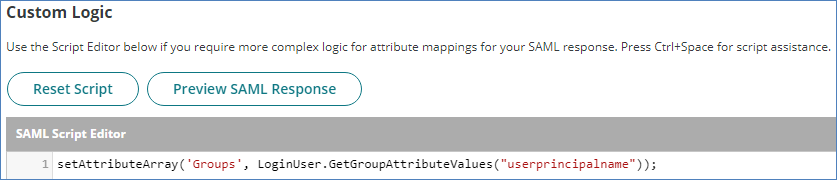
Add the following line to the SAML Script Editor, which specifies that the Groups associated with a user are sent in an attribute called "Group" in the SAML authentication response:
setAttributeArray('Groups', LoginUser.GetGroupAttributeValues("userprincipalname")); |
There are several alternate ways of sending the group information as SAML attributes in the SAML response. For example:
setAttributeArray('Groups', LoginUser.EffectiveGroupNames);
Or
setAttributeArray('Groups', LoginUser.GroupNames); |
- Do the same for the Team attributes, if needed.
- Click Save. You can use the Test button to verify the SSO token values that will be sent at runtime to
 .
.
- In
 :
:- Log in as an admin user and go to Setup > Access > Configure SAML.
- Go to the User Group Mapping tab.
- Select Map the group(s) from this SAML attribute, and fill in the group name with the name of the SAML attribute name you specified in step 2c above.

- Choose whether to update the user groups on subsequent logins.
- If needed, open the User Team Mapping tab and select the Set the User's teams from the IdP checkbox, and name the SAML Team attributes, similar to step 3c.
- Select the Service Provider Details tab and click Finish.
Dynamic Field Mapping
It is also possible to define the user fields dynamically, using similar steps to the dynamic group and team mapping. The examples below show you how to map a user's First Name and Last Name between  and Idaptive. Other field attributes are done in the same way.
and Idaptive. Other field attributes are done in the same way.
- In Idaptive:
- Open the Web App you created for accessing
 .
. - Click SAML Response to open the Custom Logic screen.
- See the example below:
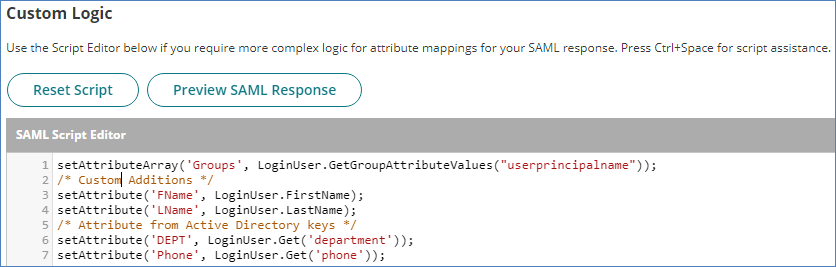
- In lines 3-4, the FName and LName attributes are used to send the user's First Name and Last Name to
 .
. - Lines 6-7 show some examples of additional values for Department and Phone Number, which can be mapped from an Active Directory or LDAP repository, which the Idaptive account is using to store user values. These examples assume that Active Directory or LDAP values of DEPT and PHONE exist.
- In
 :
:- Log in as an admin user and go to Setup > Access > Configure SAML.
- Go to the User Field(s) Mapping tab.
- Enter the values that correspond to the SAML attributes in Idaptive.

- Select the Service Provider Details tab and click Finish to save the settings.
Custom SSO URLs
By default, the  SSO login through the App List logs in as if using this URL structure with no parameters:
SSO login through the App List logs in as if using this URL structure with no parameters: https://[agiloftserver]/gui2/samlssologin.jsp?project=KB_NAME
If you need customized URLs with parameters, you can construct them based on Hyperlink Syntax and Examples and then set them up as Web Apps in Idaptive:
- Select Web Apps and click Add Web Apps.
- Select Custom Tab and click Add a Bookmark.
- Confirm and close the Add Web Apps dialogue.
- Open the new Bookmark app.
- Set the URL to your custom SSO URL. For example, if you wanted all users accessing the App to be sent to the End User Interface, you might use a URL like this with your server and KB name:
https://[agiloftserver]/gui2/samlssologin.jsp?project=KB_NAME&State=Main&euiurl=/eui2template/main.php - Click Save.
- In the User Portal, test logging in from the App List.

Force SSO Login
Finally, to make sure users log in with SSO after the transition, manually set new passwords for users who should use SSO instead. To do so:
Go to the People table and select every user who should use SSO from this point on.
Don't select every single user in your system. It's best to leave at least one administrator unchanged, if not the whole admin team, in case you encounter SSO issues in the future that prevent users from logging in with SSO. |
- Click Mass Edit, or Edit Fields, in the action bar.
- Select the Password field, then click Next to proceed to the Update tab.
- Select the formula option and enter random_password(15). This will call the random_password(15) function to randomly generate a new 15-character password for everyone you selected.
- Click Next, then Finish.
- Now, go to Setup Employees and go to the Layout tab. If you will use SSO for every user in the system, including external users, go to Setup People instead.
- Remove the Password field from the layout. This prevents users from manually setting a new password and potentially using it to log in instead of SSO.
Next, go to Setup > System > Manage Global Variables and check the Customized Variables tab for the Hotlink Type variable. If it has been customized, edit it and reset it to the default value of STANDARD.
You might also notice a setting in the People table called SSO Authentication Method. This field is set automatically by the system when you enable SSO, and should not be modified.
Related articles
|
knowledgebase. For more information on SAML configurations, see SAML 2.0 SSO. Note that the steps in this topic might vary depending on the environment in which they are being implemented. Contact
support if you need more assistance.
when they first log in with Idaptive SAML, create the users first and assign them to the appropriate Groups and Teams.




users.

knowledgebase using this URL syntax:
GUI from the Idaptive apps dashboard in the User Portal by clicking on the
SAML application icon.
SAML SSO. However, it is also possible to allocate users to different Groups or Teams from within Idaptive.


and Idaptive. Other field attributes are done in the same way.


SSO login through the App List logs in as if using this URL structure with no parameters:
